Do risk management measures and digital investment match the pace of digital disruption?
Introduction
Secure, resilient organisations no longer ask if digital disruption will affect them or their key partners, - but when. Regulators across Europe and North America share this mindset, shifting legislative and compliance priorities towards resilience, crisis readiness and supply chain fortification. Their objective: to protect critical infrastructure, economic contributors, and essential technologies – and the users who rely on them.
The focus on resilience is well-founded. The digital landscape of 2024 into early 2025 has been marked by compound disruption, where a volatile mix of geopolitical, economic, social and technological factors have combined to fuel a surge in cyber attacks. Europe and North America experienced a near 50% growth between 2023 and 2024 in disruptive and destructive cyber attacks across the two regions. These strategically significant, disruptive and destructive global cyber-attacks doubled from 103 in 2020 to 196 in 2024, and we forecast this to increase by ~20% to 233 by the end of 2025.
Businesses should now seriously consider “what if” they become the target – whether through direct attack or collateral impact from broader geopolitical tensions. This requires a proactive stance on risk management: building internal and partner resilience, developing robust crisis response capabilities, and investing in offset measures like cyber risk insurance.
Foreign policy friction, trade disputes and conflict drive ongoing systemic digital disruption
Technologies within European and North American businesses will remain vulnerable to intensifying geopolitical conflict throughout 2025 and beyond.
Increasingly antagonistic and reactionary foreign policy tensions and the rapidly evolving European security landscape are expected to inspire actions from ideologically and financially driven actors. Meanwhile these dynamics are likely to widen the divide between Western governments and their capacity to effectively deter malicious cyber activity.
The ongoing Ukraine conflict remains a primary catalyst for non-state disruptive attacks as European and North American organisations and their technologies become prime targets. Cybercriminals and activist groups are increasingly targeting these businesses simply because of the support their native countries have provided to Ukraine, or their involvement in EU security efforts. Data from Control Risks reveals a significant rise in disruptive attacks since 2022, a trend expected to persist at a similar pace through 2025.

While geopolitical tensions are key drivers of digital disruption in Europe and North America, a significantly larger proportion of attacks originate from cybercriminals (including ransomware, data leak extortion and fraud) and cyber activists (including distributed denial of service (DDoS) and hack-and-leak operations) rather than nation-state actors. Cybercriminals, in particular, are responsible for a higher volume of incidents due to their higher risk appetite, broader targeting scope, higher investment into new, sophisticated capabilities, plus a financial motive driving a higher tempo. In late-April, cybercriminal groups successfully disrupted M&S and the Co-Op – a highly disruptive campaign leaving some operations disrupted for several weeks, customer data stolen and a total cost of USD 1bn in stock market value, damages and lost revenue.[1]
Cyber activists are ideologically motivated, so less relentless than cybercriminal groups, but have been able to successfully disrupt critical infrastructure, previously causing a two-day water outage in Ireland and have also disrupted several famous brands across Europe since the start of the Ukraine conflict.

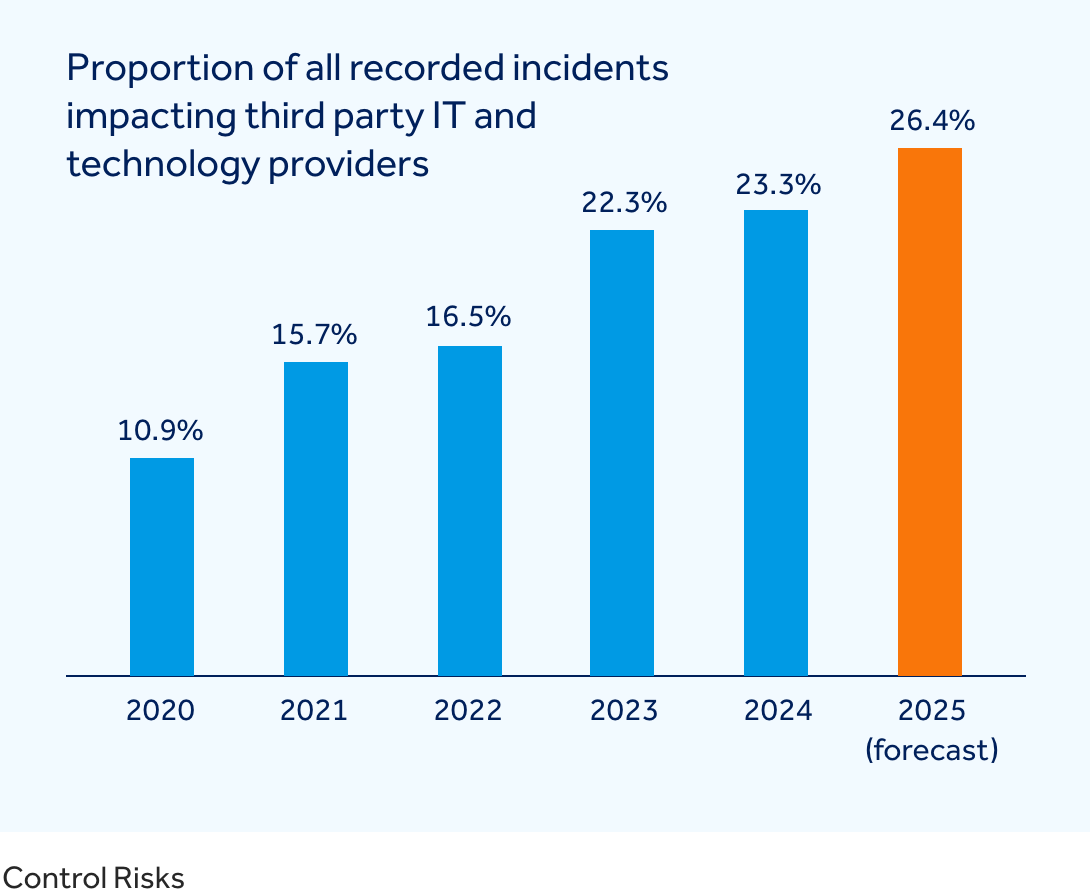
Geopolitical confrontations, including tariff policies, are placing increasing pressure on digital supply chains. These tensions push hardware acquisition costs up while driving technology providers to reassess the locations of their key operations. Additionally, technologies have become effective targets for both state and non-state actors during geopolitical conflicts, given the cascading impact on users and the substantial value they offer to criminal groups seeking to extort technology businesses and their clients. This is supported by our data, which demonstrates that across all incidents mapped in 2024, 23.3% of all those incidents impacted third party IT and technology companies. This is up from 10.9% in 2020 and is forecast to grow to 26.4% in 2025.
Rapid AI advancement fuels cyber attacks, higher success rates and boosts profits for cybercriminals
The use of AI and AI-driven marketplaces is poised to skyrocket across Europe and North America in the next five years, as generative AI (GenAI) tools deliver productivity benefits across multiple sectors.
} GenAI is projected to contribute USD 7 trillion to the global economy by 2030, driving annual productivity growth of 1.5%.[2]
} According to KPMG, GenAI could boost the UK’s productivity by 1.2% annually, adding GBP 31bn to the economy.[3]
} In response to rising demand, Microsoft plans to expand its European data centre capacity by 80% and has committed to an annual USD 80bn investment to support AI growth.[4]
However, while GenAI promises significant economic benefits, it is also being leveraged by cybercriminals to defraud and extort businesses of all sizes. This threat is already a major concern, rather than an emerging trend, with significant financial implications.
One of the most notable developments is the spike in deepfake incidents impacting, where threat actors use highly convincing deepfake videos, voices and imagery to impersonate executives, board members, and even celebrities. These manipulations trick employees into transferring large sums of money into criminally-controlled bank accounts or crypto wallets.
This trend emerged on the cyber frontlines in 2024. Control Risks observed that deepfakes were used in nearly 10% of all successful cyber incidents, with losses ranging from USD 250,000 to over USD 20m and an average loss of USD 500,000 to 1m.[5]
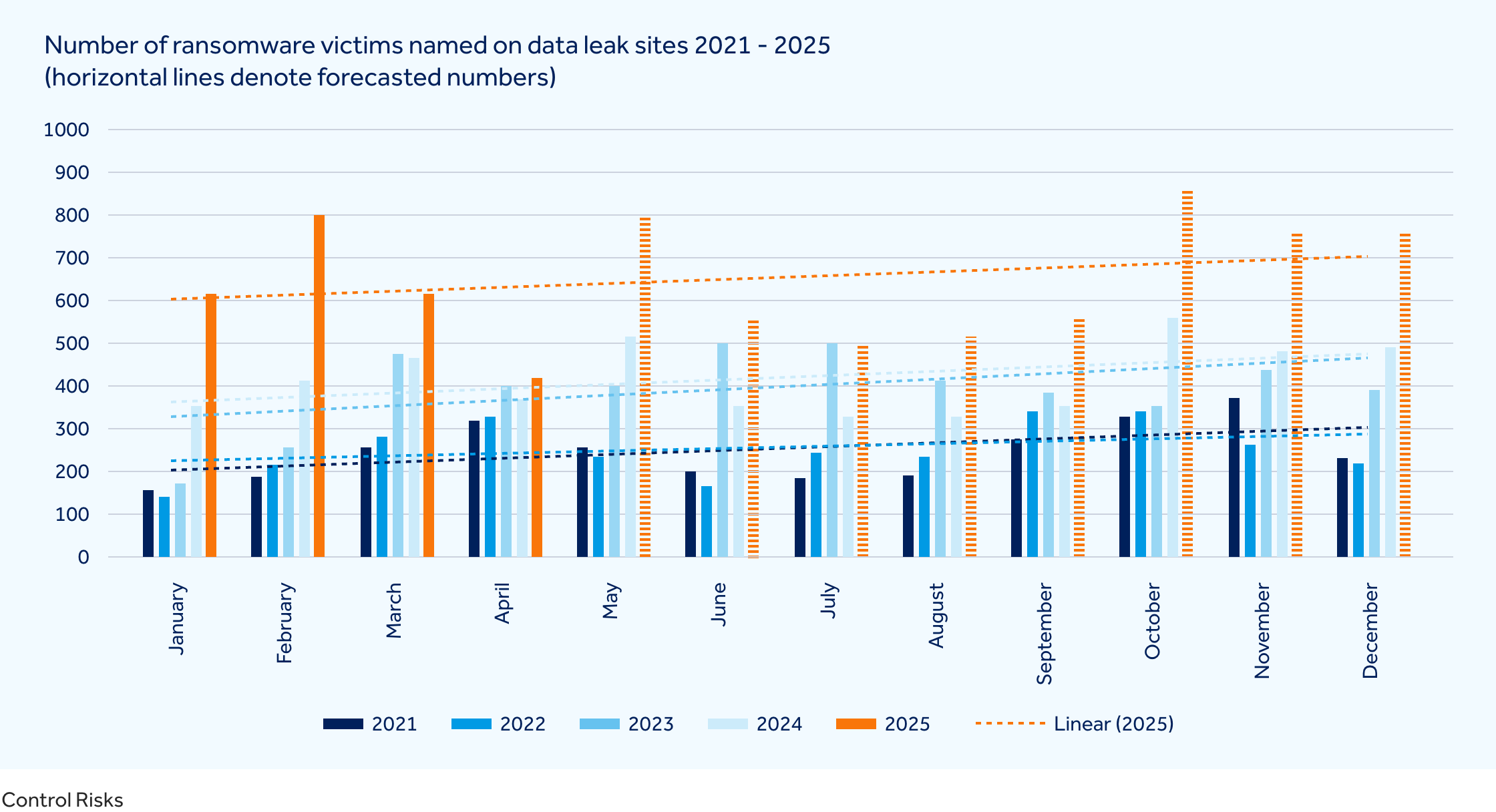
Non-AI cybercriminal attacks are also on the rise, fuelled by AI tools that improve the end-to-end capabilities of malicious actors. These tools enable more personalised, convincing phishing emails and significantly accelerate malware generation and distribution. This trend is particularly evident in the profit-driven cybercriminal sphere, in which 2025 has already seen a 54% increase in the number of publicly identified ransomware extortion victims compared to the same period in 2024 (January-April).[6]
As businesses integrate AI tools into their operations - whether for internal use or to support customer needs - it’s crucial to assess how these innovations may introduce or drive future risks. AI systems are increasingly targeted by malicious actors to steal data, extort victims and disrupt organisational technologies. Below are some of the key attack methods we are observing, which are expected to impact GenAI tools in 2025.

Digital risk landscape in numbers
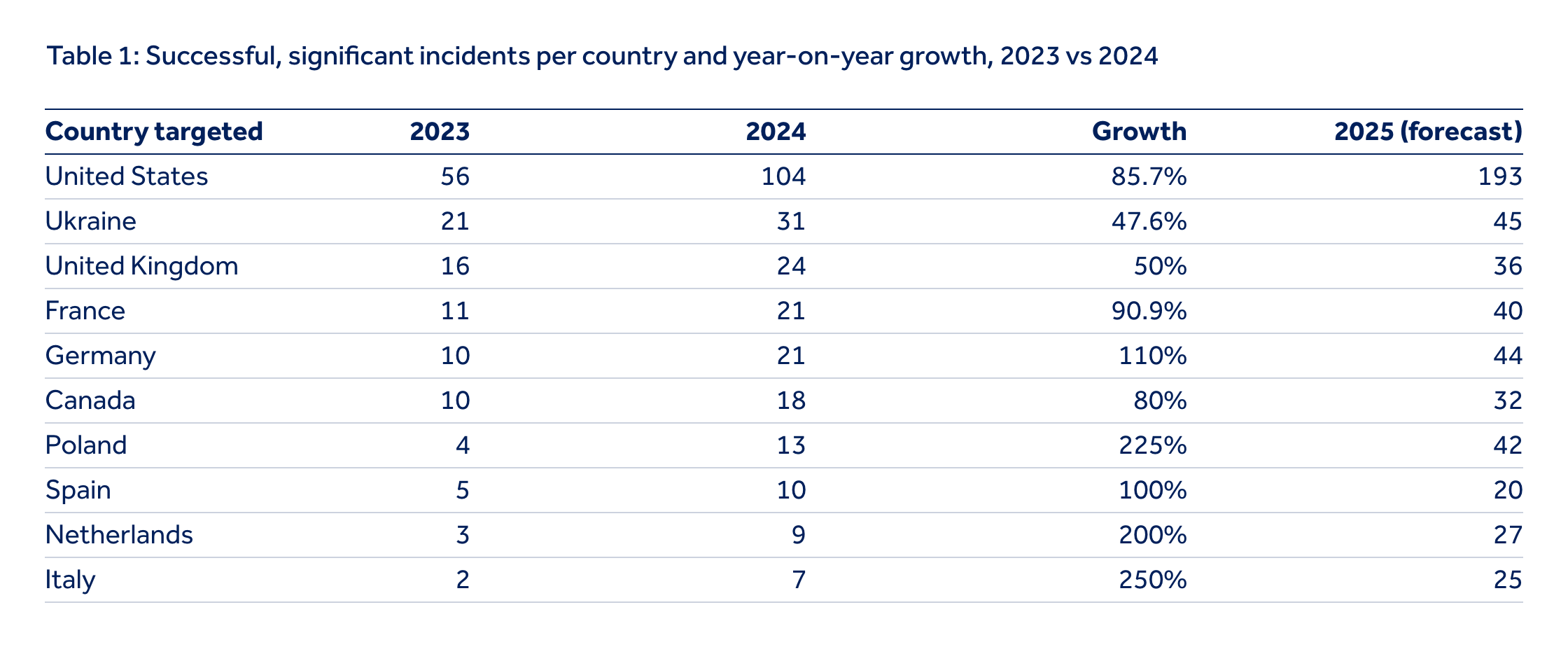
Between 2023 and 2024, we observed a 42% increase in successful, significant cyber incidents across Europe and North America – driven by the geopolitical, socioeconomic and technological factors outlined above. Italy, the Netherlands, Poland, Germany, Spain and France have each experienced approximately 50% year-on-year growth in such incidents. This spike is largely linked to their support for Ukraine and active roles in European security, making them key targets for cybercriminals and activist groups. These actors are disrupting organisations through ransomware, website defacement, DDoS and hack-and-leak campaigns.
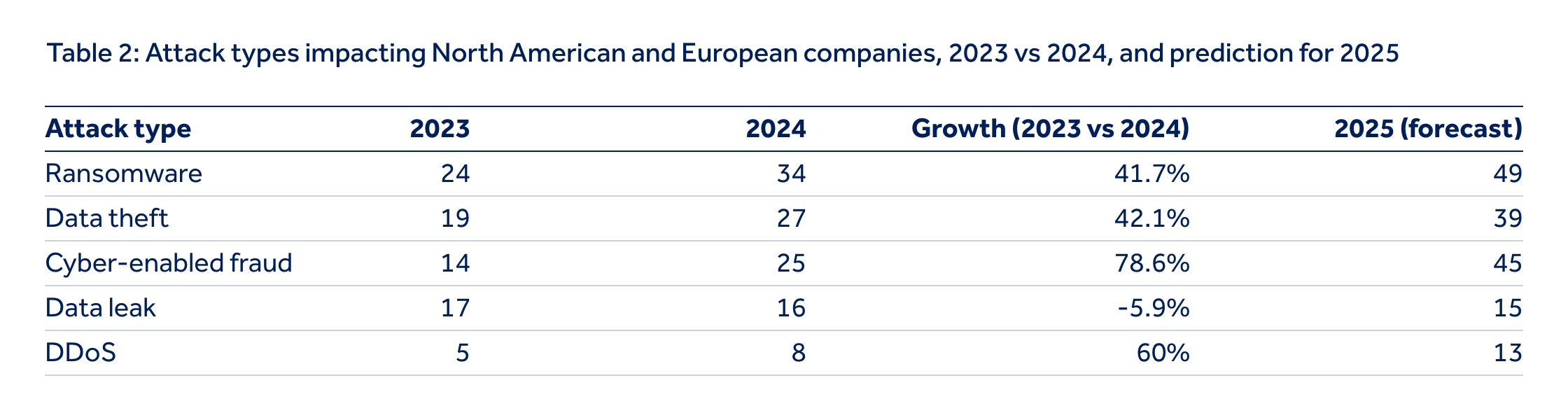
When examining the types of incidents impacting companies in Europe and North America - particularly those driven by non-state activity - there is clear year-on-year growth in disruptive ransomware attacks, cyber-enabled fraud and data theft. While the financial impact of these incidents varies by region and attack type, the average cost of a data breach illustrates the scale of the risk: USD 4.27m[7] in Europe compared to USD 9.26m in the US.[8]
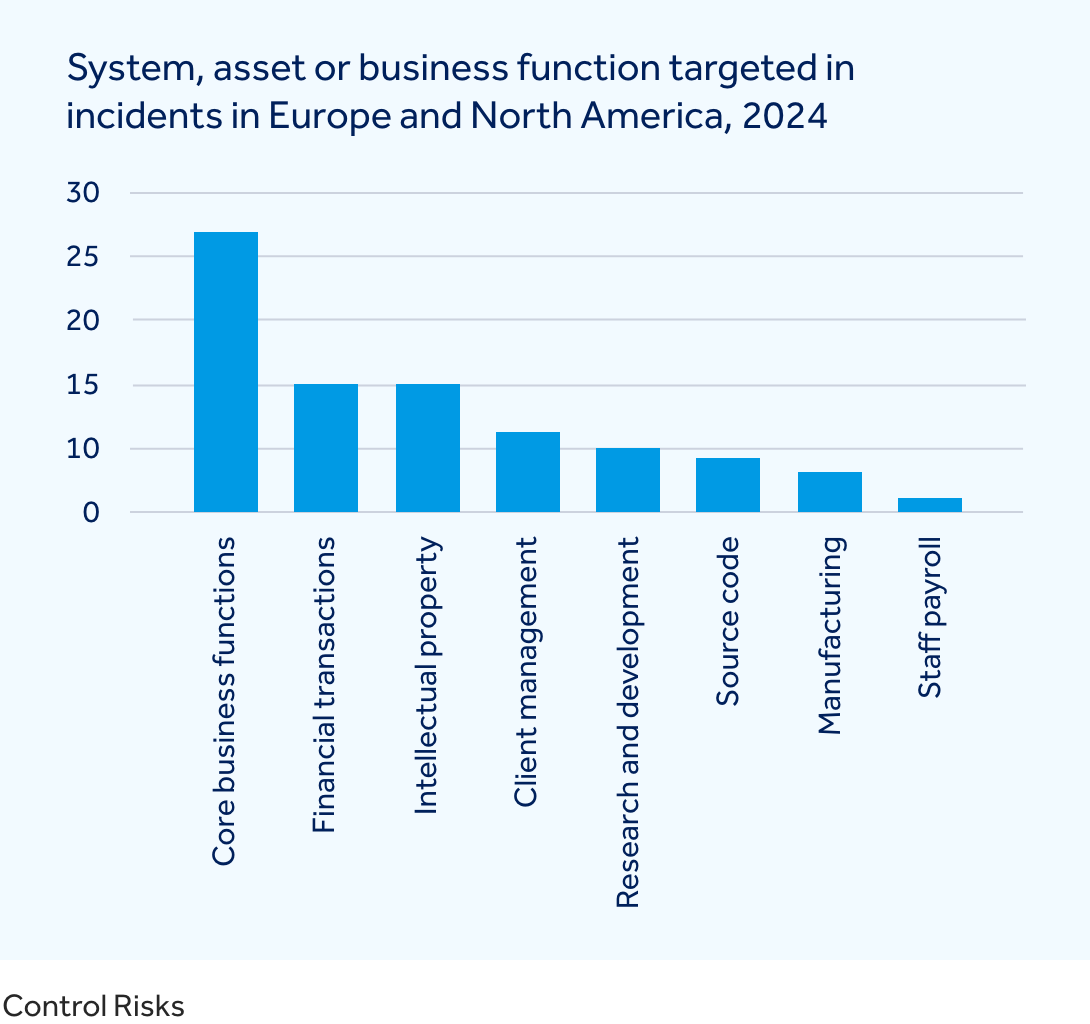
In Europe and North America, cyber attacks most consistently target core business functions and systems, including email, file share systems, messaging apps and other central corporate apps. Financial transactions are the second most commonly targeted area, with deepfakes exploited to deceive finance teams and approvers and higher rates of successful fraud. Beyond these, threat actors continue to pursue high value assets including research data, intellectual property and client management systems, which offer considerable appeal to both financially and ideologically motivated attackers.
Navigating digital challenges
Effective risk management requires organisations to first identify their most critical data assets and technologies. This enables efficient prioritisation of their security investments, alongside ongoing improvements to security controls, monitoring, and overall network resilience.
Understanding which systems and applications drive revenue and support growth is essential when deciding which technology priorities to invest in first. This also informs decisions on engagement with the key third parties who support those technologies and ensure contingency plans are in place if critical systems go offline.
Redundancy planning is vital, and while full duplication of cloud infrastructure may not be possible, a combination of robust business continuity planning, selective duplication of key systems and a well-prepared crisis management team can significantly reduce risk.
No matter the scale, any cyber incident will cost your business time, resources and opportunity. It’s vital to regularly review insurance coverage to ensure it reflects an increasingly disruptive and unpredictable threat landscape.
[1] https://news.sky.com/story/mands-warns-of-300m-profit-hit-due-to-hacking-crisis-13371908



